426AF0 is the beginning of the Behemoth's behavior function. This function controls how the Behemoth moves and acts.
After the little
PUSH EBP and MOV EBP,ESP portion, you should see a really big pile of MOV instructions. These are the framerects, the stuff that will control which sprites from the Cave Story spritesheets that the NPC will use.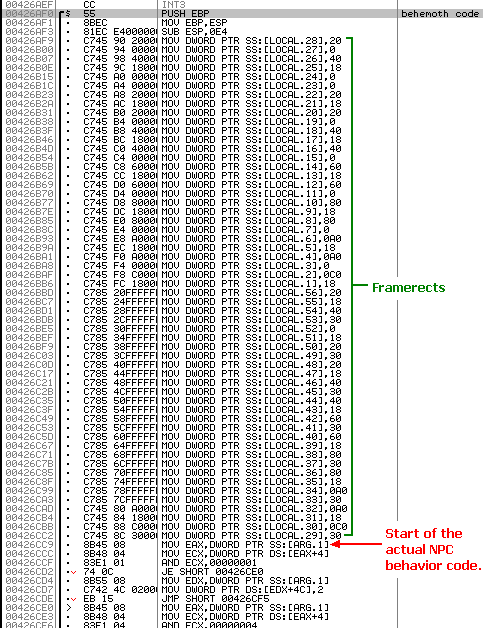
So, what does [LOCAL.28] or [ARG.1] mean?
[ARG.1] means "argument 1", the argument last PUSHed before CALLing this function. That means [ARG.1] stands for [EBP+8]. All of the [LOCAL.(number)] parts are actually local variables. The framerects for the Behemoth are stored into a big list of local variables. We will talk about the difference between local and global variables later on.
I'm now going to tell you how to change the notation that OllyDbg gives you. Double click on the MOV instruction located at 426AF9 (the start of the behemoth framerects). Once the instruction-editing window pops up, DON'T edit anything. Just click "Assemble". Now, don't close the small window. Keep clicking "Assemble" repeatedly. If you did everything correctly, the code should now look like this:

All the [LOCAL]s have been replaced with [EBP-(some number)] and all [ARG.1]s are now [EBP+8].
The NPC Object Pointer
If we're building a function, we know that we can access the value of the last argument PUSHed by looking inside [EBP+8]. Now, what does the behemoth (or any other NPC) use [EBP+8] for?
Whenever we do NPC hacking, we can look inside the memory location [EBP+8] to find a special address. This address is the pointer to the NPC object.
Aha! So now we can talk about objects (as in object-oriented programming) without diving into all that abstract junk. Objects are real structures that you can modify and control using ASM code, and that's exactly how we're going to hack NPCs.
Previous Lesson: Object Oriented Programming
Next Lesson: NPC Hacking 2
Table of Contents